OpenID Connect
Summary
This short series of steps enables admins to connect their identity providers using OpenID Connect (OIDC) to Bigeye for single sign on. Upon completion, your employees will be able to login to Bigeye using your identity provider.
Bigeye OIDC only supports connecting via a Client ID and Client Secret. It does not support via a private JWT token at this time.
Configure your identity provider for Bigeye
This step will help you configure your identity provider to integrate with Bigeye for single sign on.
Specific instructions can be found for the following identity provider types:
To connect to Bigeye, you may need to configure the following settings in your identity provider:
Note - substitute the email domain valuesMake sure to enter the same
<domain>value throughout this process. The domain will be the email domain of your users such asexample.com. If you have more than one domain, it is recommended to set up more than one connection inside of Bigeye.
Note - your Bigeye URL may be differentIf you use a Bigeye URL that is different from app.bigeye.com, please substitute your Bigeye URL while performing the steps of this configuration.
- Signin Redirect URIs - set to
https://app.bigeye.com/sso/oidcLogin/<domain>These are allowed signin URIs for single sign-on from Bigeye. - Return URL - set to
https://app.bigeye.com/sso/<domain> - Initiate Login URL - set to
https://app.bigeye.com/sso/<domain>. This is used by identity providers to provide a home screen with one-click access into Bigeye. - Application type - set to
web application. This is useful because Bigeye's application servers will verify single sign-on attempts without revealing secrets to the user's browser. - Grant type - set to
Authorization CodeandRefresh Token - Scopes - set to add the
openid,profile,email, andoffline_accessscopes. Bigeye uses thenameandemailfields to generate the user's account upon first login. To expose groups to Bigeye, add thegroupsscope.
Bigeye will need three things from your identity provider to set up the connection:
- Issuer URL - this is a URL that provides information about your OIDC endpoints and which parameters are accepted. This URL should be accessible over the network that connects to Bigeye. Bigeye will append
.well-known/openid-configurationto the URL you provide. - Client ID - this is the authentication token ID used when validating user logins from your identity provider
- Client Secret - this is the authentication token secret used when validating user logins from your identity provider
Configure Bigeye for your identity provider
To configure Bigeye for your identity provider:
- Go to https://app.bigeye.com/settings/single-sign-on
- Click New Connection
- Set the following values:
- Single sign-on provider: OpenID Connect (OIDC)
- Domain: your email domain (e.g. example.com). After this connection is activated, all email addresses for this email domain will be forwarded to your identity provider.
- Connection name: your email domain (e.g. example.com). This is an identifier used by Bigeye and your identity provider when they interact.
- Issuer URL: this is the URL that provides information about your OpenID Connect endpoints and which parameters are accepted. This URL should be accessible over the network that connects to Bigeye. Bigeye will append
.well-known/openid-configurationto the URL you provide. - Client ID and Client Secret as configured by your identity provider
- Click Save
Once the connection is saved, all logins for the domain specified will be validated by your identity provider. We highly recommend doing the following to verify your connection:
- Log in inside of another browser to verify that you can log in. If you are not able to log in, you may delete the Single Sign-on Connection inside of Bigeye to prevent other users from being locked out.
- Verify in your identity provider that the correct users are added to the applicable membership groups for Bigeye.
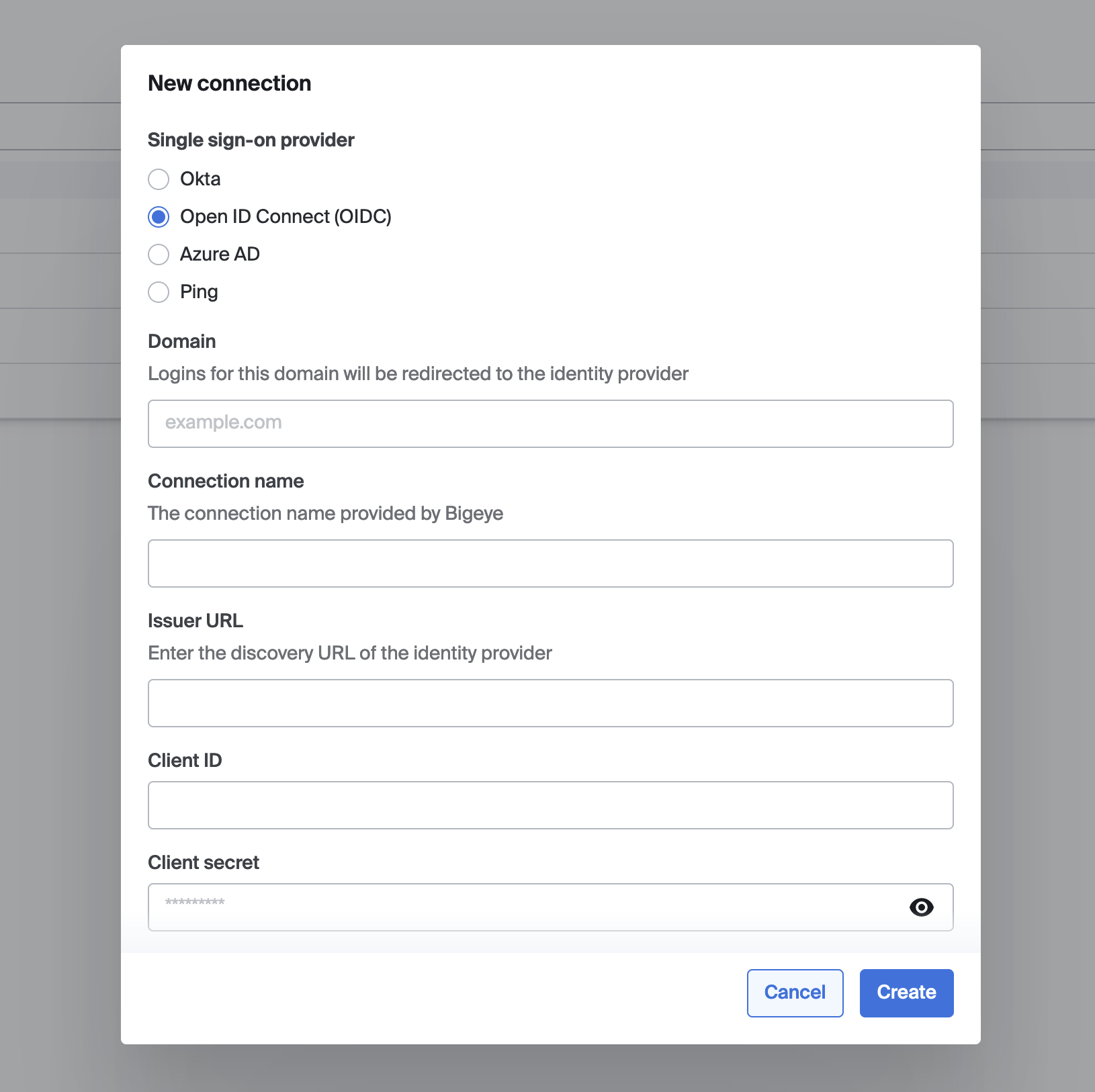
Configuration dialog for a new single sign-on connection
Account Creation, Validation, and Deactivation
- Bigeye will create accounts as needed for users, but it will not automatically add them to any workspaces. To control user access into Bigeye, we recommend applying group membership policies inside of your identity provider. Steps for this process can be found on the mapping IDP SSO groups to Bigeye groups page.
- When users are deactivated or removed inside of your identity provider for any reason, they are not removed from Bigeye. However, they will no longer be able to log in through your identity provider.
- User sessions are revalidated and re-authenticated every hour with your identity provider or when an expiration (expires_at) is passed with a token if it is more frequent than an hour.
- If a user's access is removed from Bigeye through your group policy, they will maintain access until their session is revalidated.
- Bigeye does not force re-authentication when roles change.
Updated 5 months ago
